Private VLAN (PVLAN)
Here you will find answers to Private VLAN Questions
Quick review:
The main purpose of Private VLAN (PVLAN) is to provide the ability to isolate hosts at Layer 2 instead of Layer 3. As you know, a VLAN is a broadcast domain, by using PVLAN we are splitting that domain into some smaller broadcast domains. For example, without PVLAN, a service provider wants to increase security by isolating customers into separate domains so that they can’t access each other, they have to assign them into different VLANs and use different subnets. This can result in a waste of IP addresses and difficulty in VLAN management. Private VLANs (PVLANs) can solve this problem by allowing the isolation of devices at Layer 2 in the same subnet. PVLAN can be considered “VLANs inside VLAN”.
There are three types of ports in PVLAN:
* Isolated: only communicate with promiscuous ports. Notice that it cannot even communicate with another isolated port. Also, there can be only 1 isolated VLAN per PVLAN.
* Promiscuous: can communicate with all other ports. The default gateway is usually connected to this port so that all devices in PVLAN can go outside.
* Community: can communicate with other members of that community and promiscuous ports but cannot communicate with other communities. There can be multiple community VLANs per PVLAN.
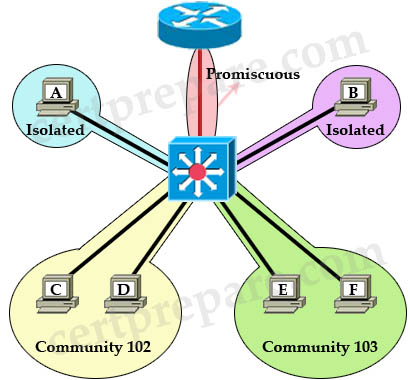
For example, in the topology above:
+ Host A cannot communicate with Host B, C, D, E and F. It can only communicate with Promiscuous port to the router. Notice that even two Isolated ports in the same VLAN cannot communicate with each other.
+ Host C can communicate with Host D because they are in the same community but Host C cannot communicate with E and F because they are in a different community.
+ All hosts can go outside through promiscuous port.
Also I want to mention about the concept of “primary VLAN” and “secondary VLAN”. PVLAN can have only one primary VLAN; all VLANs in a PVLAN domain share the same primary VLAN. Secondary VLANs are isolated or community VLANs.
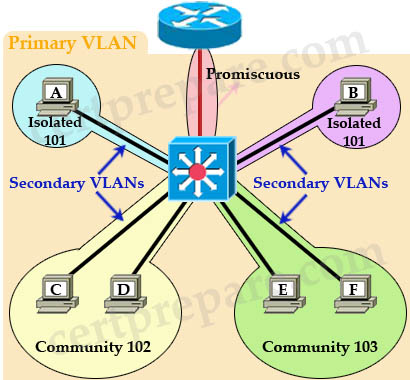
Configuration of PVLAN:
1. Set VTP mode to transparent
2. Create secondary (isolated and community) VLANs and primary VLAN
3. Associate secondary VLANs to the primary VLAN
4. Configure interfaces as promiscuous interfaces
5. Configure interfaces to be isolated or community interfaces.
Sample configuration used the topology above:
//First set VTP to transparent mode
Switch(config)#vtp mode transparent
//Create secondary VLANs
Switch(config)#vlan 101
Switch(config-vlan)#private-vlan isolated
Switch(config-vlan)#vlan 102
Switch(config-vlan)#private-vlan community
Switch(config-vlan)#vlan 103
Switch(config-vlan)#private-vlan community
//Create primary VLAN
Switch(config-vlan)#vlan 100
Switch(config-vlan)#private-vlan primary
//Associate secondary (isolated, community) VLANs to the primary VLAN
Switch(config-vlan)#private-vlan association 101,102,103
//Assign Promiscuous port to the port connected to the router, with the primary VLAN mapped to the secondary VLAN.
Switch(config)# interface f0/1
Switch(config-if)# switchport mode private-vlan promiscuous
Switch(config-if)# switchport private-vlan mapping 100 101,102,103
//Ports connected to hosts A, B, C, D, E, F are configured in host mode and assign to appropriate VLANs (A and B to isolated VLAN 101; C and D to community VLAN 102; E and F to community VLAN 103):
Switch(config)# interface range f0/2 – 0/3 //connect to host A and B
Switch(config-if)# switchport mode private-vlan host
Switch(config-if)# switchport private-vlan host-association 100 101
Switch(config-if)# interface range f0/3 -0/4 //connect to host C and D
Switch(config-if)# switchport mode private-vlan host
Switch(config-if)# switchport private-vlan host-association 100 102
Switch(config-if)# interface f0/5 – 0/6 //connect to host E and F
Switch(config-if)# switchport mode private-vlan host
Switch(config-if)# switchport private-vlan host-association 100 103
To check the configuration, use this command:
Switch# show vlan private-vlan
Question 1
Refer to the exhibit. The web servers WS_1 and WS_2 need to be accessed by external and internal users. For security reasons, the servers should not communicate with each other, although they are located on the same subnet. The servers do need, however, to communicate with a database server located in the inside network. What configuration will isolate the servers from each other?
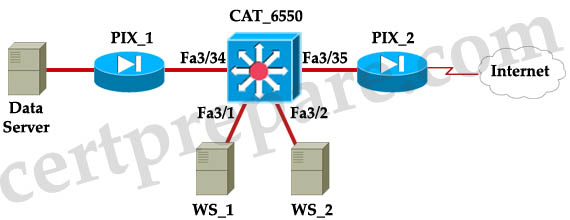
A. The switch ports 3/1 and 3/2 will be defined as secondary VLAN community ports. The ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.
B. The switch ports 3/1 and 3/2 and the ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.
C. The switch ports 3/1 and 3/2 and the ports connecting to the two firewalls will be defined as primary VLAN community ports.
D. The switch ports 3/1 and 3/2 will be defined as secondary VLAN isolated ports. The ports connecting to the two firewalls will be defined as primary VLAN promiscuous ports.
Answer: D
Explanation
WS_1 and WS_2 cannot communicate with each other so we can put them into isolated ports. Isolated ports can only communicate with promiscuous ports so Fa3/34 and Fa3/35 should be promiscuous ports so that they can send and receive data with the Data Server.
Note: Answer A is not clear because it does not state the switch ports 3/1 and 3/2 are put into the same or different VLAN community ports. If they are put into different VLAN communities then answer A is correct.
Question 2
Refer to the exhibit. What can be concluded about VLANs 200 and 202?

A. VLAN 202 carries traffic from promiscuous ports to isolated, community, and other promiscuous ports in the same VLAN. VLAN 200 carries traffic between community ports and to promiscuous ports.
B. VLAN 202 carries traffic from promiscuous ports to isolated, community, and other promiscuous ports in the same VLAN. VLAN 200 carries traffic from isolated ports to a promiscuous port.
C. VLAN 200 carries traffic from promiscuous ports to isolated, community, and other promiscuous ports in the same VLAN. VLAN 202 carries traffic between community ports and to promiscuous ports.
D. VLAN 200 carries traffic from promiscuous ports to isolated, community, and other promiscuous ports in the same VLAN. VLAN 202 carries traffic from isolated ports to a promiscuous port.
Answer: B
Explanation
In fact the exhibit above is wrong, that output should be from the command “show vlan private-vlan”. The “show vlan private-vlan type” should give output like this:
| Vlan | Type |
| 202 200 |
Primary isolated |
With this output we can see VLAN 202 is configured as the primary VLAN while VLAN 200 is configured as secondary (isolated) VLAN -> B is correct.
Question 3
Private VLANs can be configured as which three of these port types? (Choose three)
A. isolated
B. protected
C. private
D. associated
E. promiscuous
F. community
Answer: A E F
Explanation
There are three types of ports can be configured in a Private VLAN: isolated, promiscuous, community.
* Isolated: only communicate with promiscuous ports. Notice that it cannot even communicate with another isolated port. Also, there can be only 1 isolated VLAN per PVLAN.
* Promiscuous: can communicate with all other ports. The default gateway is usually connected to this port so that all devices in PVLAN can go outside.
* Community: can communicate with other members of that community and promiscuous ports but cannot communicate with other communities. There can be multiple community VLANs per PVLAN.
Question 4
Refer to the exhibit. From the configuration shown, what can you determine about the private VLAN configuration?
| Switch# configure terminal Switch (config)# vlan 20 Switch (config-vlan)# private-vlan primary Switch (config-vlan)# exit Switch (config)# vlan 501 Switch (config-vlan)# private-vlan isolated Switch (config-vlan )#exit Switch (config)# vlan 502 Switch (config-vlan)#private-vlan community Switch (config-vlan)# exit Switch (config)# vlan 503 Switch (config-vlan )# private-vlan community Switch (config-vlan)# exit Switch (config)# vlan 20 Switch (config-vlan)#private-vlan association 501-503 Switch (config-vlan)# end |
A. Only VLAN 503 will be the community PVLAN because multiple community PVLANs are not allowed.
B. Users of VLANs 501 and 503 will be able to communicate.
C. VLAN 502 is a secondary VLAN.
D. VLAN 502 will be a standalone VLAN because it is not associated with any other VLANs.
Answer: C
Explanation
There are two types of secondary VLAN: isolated and community. In this case VLAN 502 is a community VLAN -> C is correct.
In a PVLAN, multiple community VLANs are allowed. But notice a PVLAN can have only one primary VLAN and one isolated VLAN -> A is not correct.
Only community in the same VLAN can communicate with each other. Users in different communities are not able to communicate -> B is not correct.
The command “private-vlan association 501-503” associates VLANs 501, 502 and 503 to the Primary VLAN 20 -> D is not correct.
Question 5
When configuring private VLANs, which configuration task must you do first?
A. Configure the private VLAN port parameters.
B. Configure and map the secondary VLAN to the primary VLAN.
C. Disable IGMP snooping.
D. Set the VTP mode to transparent.
Answer: D
Explanation
Before configuring private VLANs, we must set VTP mode to transparent because VTP version 1 and 2 do not support private VLAN (VTP version 3 does support PVLAN). Notice that a switch in VTP transparent mode still forwards other VTP updates to its neighbors.
Question 6
A switch has been configured with Private VLANs. With what type of PVLAN port should the default gateway be configured?
A. Trunk
B. Isolated
C. Primary
D. Community
E. Promiscuous
Answer: E
Explanation
A default gateway should be configured Promiscuous type so that all devices in PVLAN can go outside.


